Cybersecurity Services
Secure your digital future with proactive, adaptive and intelligent defense.

Safeguard your data, systems, and user with end to end cybersecurity solutions - from threat prevention and detection to incident response and compliance.
What We Offer
Vulnerability Assessment & Penetration Testing (VAPT)
Identify security flaws early through expert-led manual and automated testing to outpace potential attackers.
Network Security & Firewall Management
Protect internal networks from threats using enterprise-grade firewalls, intrusion detection, and anti-malware defense systems.
Cloud Security & Configuration Hardening
Secure cloud infrastructure (AWS, Azure, GCP) with identity control, encryption policies, and compliance-ready configurations.
Endpoint Detection & Response (EDR)
Continuously monitor devices for threats with advanced EDR tools, and respond to incidents in real time.
Security Information & Event Management (SIEM)
Gain full visibility into your infrastructure with real-time log monitoring, anomaly detection, and automated alerts.
Compliance & Risk Management
Meet global standards (ISO 27001, GDPR, HIPAA, PCI-DSS) with tailored audits, gap analysis, and policy implementation.
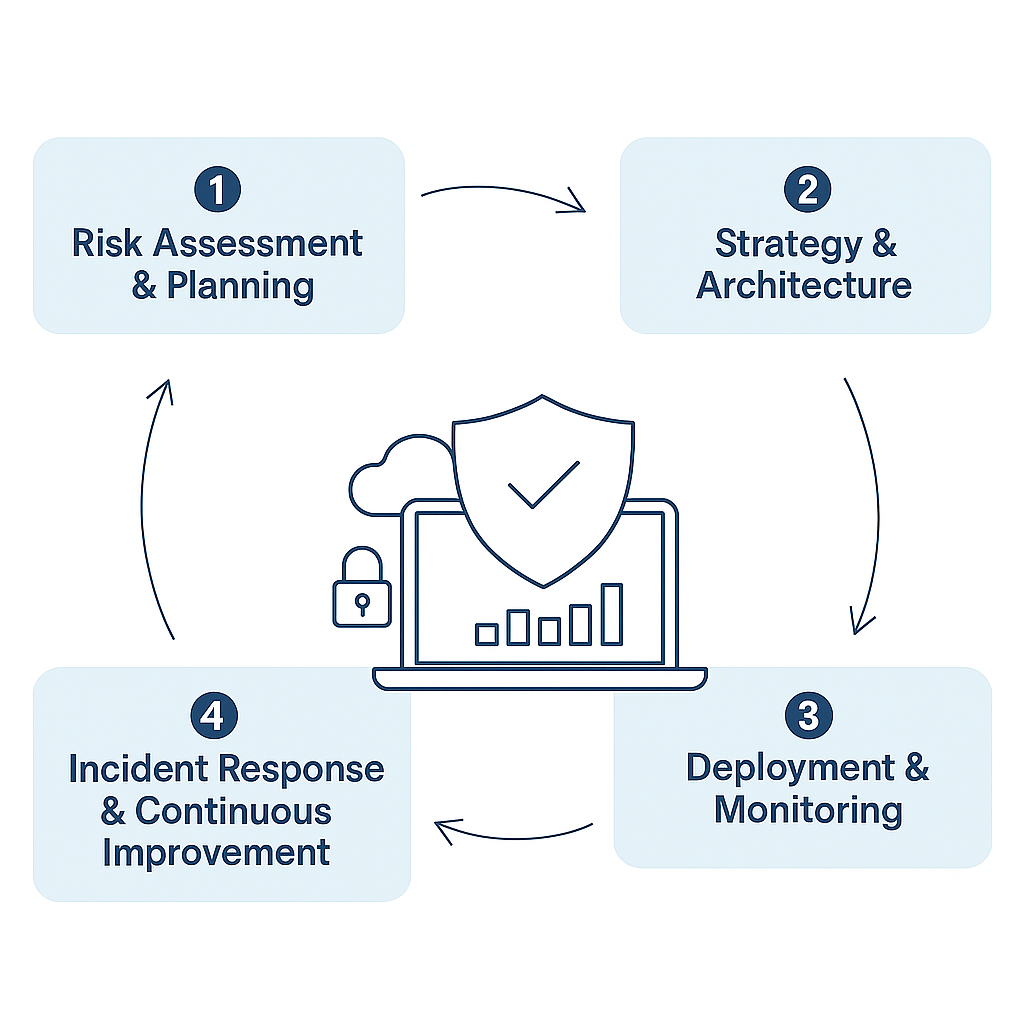
Our Process
A proactive framework for protection, resilience, and continuous enhancement.
Technologies We Work With
We secure your digital world using industry-leading, advanced, and battle-tested cybersecurity technologies trusted by global enterprises.
Tools & Platforms
SPLUNK
FORTINET
WIRESHARK
Cloud & Infra Security
AZURE SECURITY CENTRE
AWS IAM
PRISMA CLOUD
SIEM & ED
IBM Q RADAR
MICROSOFT DEFENDER
SENTINEL ONE
Compliance Tools
VANTA
DRATA
NIST CSF
Languages & Scripting
POWERSHELL
BASH
PYHTON
Work Showcase
Protecting What Matters Most: Your Data, Our Mission.
Client Testimonials


Let’s Secure What Matters Most!!
Whether you’re scaling or just getting started — our cybersecurity experts ensure you’re protected from all angles.
Frequently Asked Question
Yes. While cloud providers secure the infrastructure, you’re responsible for securing your data, applications, and user access.
Absolutely. We offer audits, documentation support, and technical implementation aligned with regulatory standards.
We provide immediate incident response, root cause analysis, recovery planning, and prevention of future threats.
It provides a comprehensive range of cybersecurity services, including vulnerability assessment, penetration testing, cloud security, endpoint protection, threat monitoring, and incident response. We tailor each solution to your business needs for maximum protection.
We use advanced SIEM tools and AI-powered monitoring systems that detect and respond to anomalies in real-time. Our security operations center (SOC) operates 24/7 to provide continuous oversight and immediate action against potential threats.
Absolutely. Our solutions are scalable and cost-effective, designed to protect organizations of all sizes. We work closely with SMBs to implement right-sized security frameworks that balance budget, risk, and compliance.
